Every blockchain needs a way for thousands of computers to agree on which transactions are valid. This agreement process is called a consensus mechanism, and it is what keeps the ledger honest without a central authority. Proof of Stake (PoS) is one of the main consensus designs used today. Instead of burning electricity like Proof of Work mining, PoS asks participants to lock up coins as a kind of security deposit and rewards them for behaving honestly. Ethereum’s move to Proof of Stake in “the Merge” made PoS impossible to ignore. Many newer smart contract platforms, like Solana and Cardano, also rely on PoS or its variants. In this guide you will learn how PoS works in practice, how validators are chosen, where staking rewards come from, and what risks like slashing and lock-ups mean. You will also see how PoS compares to Proof of Work so you can make more informed decisions about staking and network participation.
Key Takeaways About Proof of Stake
Summary
- Proof of Stake secures a blockchain by having participants lock coins as stake, which can be rewarded for honest behavior or partially lost for cheating or going offline.
- Validators are chosen using a pseudo-random process that usually favors those with more stake, then they propose and attest to new blocks of transactions.
- PoS is far more energy-efficient than Proof of Work because it relies on capital at risk, not continuous high-power hardware and electricity use.
- Staking rewards typically come from new token issuance and transaction fees, and real returns depend on factors like total stake, validator performance, and network activity.
- Main risks include slashing, downtime penalties, lock-up or unbonding periods where you cannot move your coins, and smart contract or custody risk when using third-party services.
- You can participate at different levels, from running your own validator to simply delegating stake or using exchange and liquid staking services, each with its own trade-offs.
Proof of Stake in Everyday Language
- Validators lock up coins as stake and run software that proposes and validates blocks of transactions.
- Delegators keep control of their coins but assign their staking power to a validator or pool to help secure the network.
- Honest participants earn staking rewards paid in the network’s native token, often compounding over time if restaked.
- Dishonest or unreliable participants can face slashing or reduced rewards, losing part of their stake or missing income.
How Proof of Stake Actually Works
- Rewards distribution: Honest validators and their delegators receive rewards, usually proportional to their stake and uptime, paid out at regular intervals or epochs.
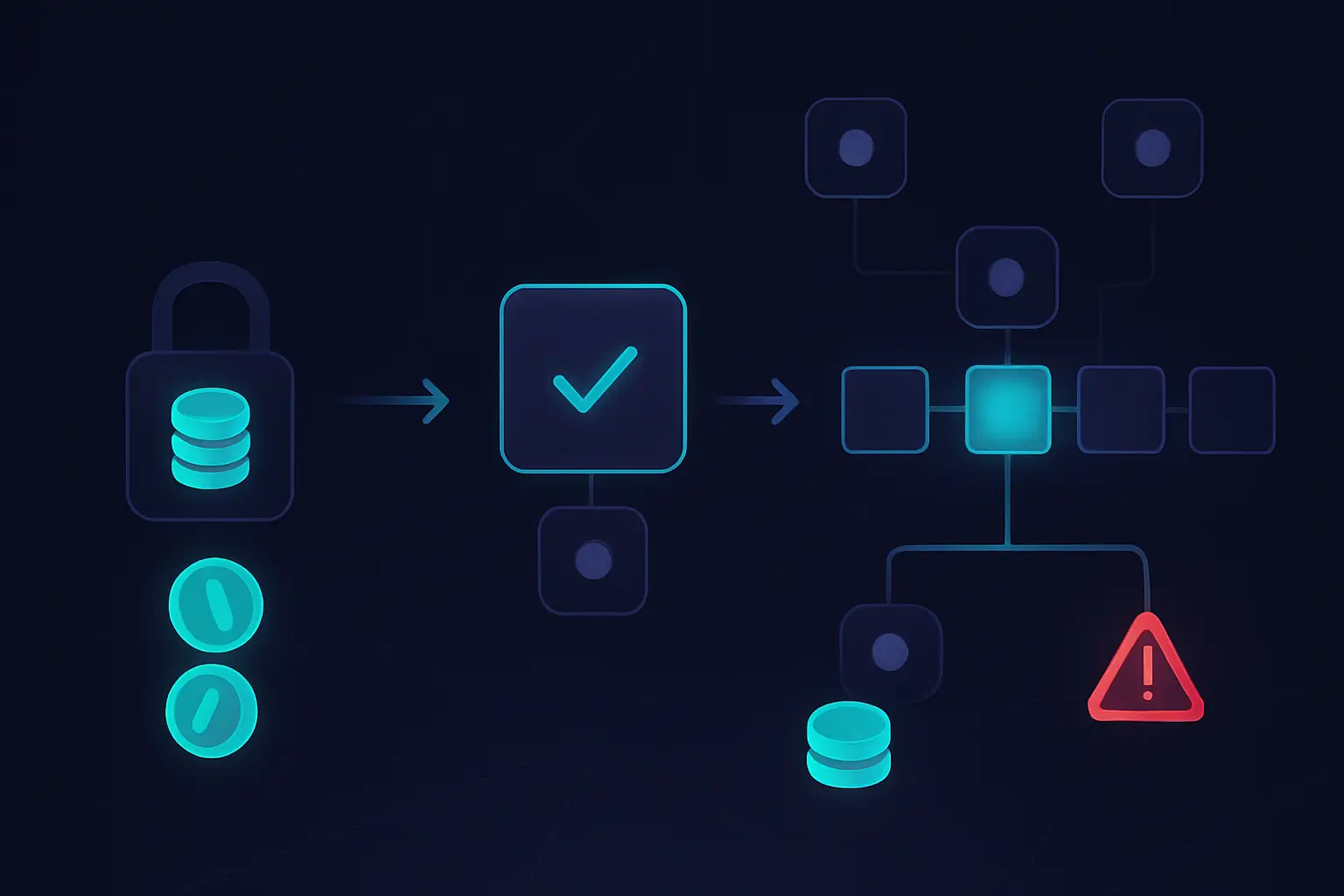
Roles in a Proof of Stake Network
Key facts

Pro Tip:Even if you only act as a delegator, you still share risk with your chosen validator or pool. If they are slashed or frequently offline, your rewards can drop and in some networks your stake can be directly affected. Research validator performance, fees, and reputation instead of simply chasing the highest advertised yield.
What Proof of Stake Is Used For
Today, many of the most active smart contract platforms are secured by Proof of Stake. This includes networks where people trade tokens, mint NFTs, lend and borrow, and deploy decentralized applications. Because PoS affects how quickly blocks are produced and how many validators participate, it influences transaction fees, confirmation times, and overall network capacity. It also creates staking opportunities that let long-term holders earn rewards while contributing to security. When you use DeFi protocols, NFT marketplaces, or bridges on a PoS chain, you are indirectly relying on its staking system to keep your transactions safe and final.
Use Cases
- Securing smart contract platforms like Ethereum, Solana, and Cardano, where validators ensure that complex on-chain programs execute correctly.
- Enabling relatively low-fee, fast transactions by coordinating block production without the heavy energy costs of mining.
- Powering DeFi protocols and NFT ecosystems that depend on reliable finality and predictable block times.
- Providing staking income opportunities for long-term token holders who are willing to lock or delegate their coins.
- Supporting on-chain governance where staked tokens can be used to vote on protocol upgrades and parameter changes.
- Anchoring sidechains and Layer 2 networks that use PoS variants to inherit security from a base chain or coordinate their own validators.
Case Study: Ravi’s First Steps into Proof of Stake

Rewards, Inflation, and Economics of PoS
- Total amount staked: When more tokens are staked, the same reward pool is spread across more participants, often lowering individual APR.
- Inflation schedule: Protocol rules for how many new tokens are issued per block or per year directly shape baseline staking yields.
- Transaction volume and fees: Busy networks with high fees can boost rewards, while quiet periods may reduce them.
- Validator performance: Uptime, correct behavior, and low error rates help maximize rewards for a validator and its delegators.
- Protocol parameters: Settings like minimum stake, reward curves, and penalties are regularly tuned through governance and upgrades.
Pro Tip:Headline staking APRs are only part of the picture. Your real outcome depends on token price moves, how long your funds are locked, whether rewards are auto-compounded, and the chance of slashing or downtime. Always compare potential yield with the risks and your own time horizon, not just the biggest percentage on a website.
Risks and Security Considerations in Proof of Stake
Primary Risk Factors
Proof of Stake avoids the massive energy consumption of mining, but it introduces a different set of risks. Instead of hardware failures and electricity bills, you face slashing, smart contract bugs, custody issues, and governance problems. Because stake can concentrate in large validators, exchanges, or liquid staking protocols, PoS networks also worry about centralization of voting power. Long lock-up or unbonding periods can make it hard to react quickly if something goes wrong. Understanding these risks helps you choose safer staking methods and avoid treating staking as a no-brainer savings account.
Primary Risk Factors
Security Best Practices
Strengths and Weaknesses of Proof of Stake
Pros
Cons
Proof of Stake vs. Proof of Work
Ways to Participate in Proof of Stake
- Running your own validator: Highest control and direct rewards, but requires technical skills, reliable hardware, and careful monitoring to avoid slashing.
- Delegating via native wallets: You keep your keys and simply choose one or more validators, making it relatively easy while still sharing some validator risk.
- Staking through centralized exchanges: Very simple one-click experience and no node management, but you hand over custody and concentrate power in large platforms.
- Using liquid staking tokens: You stake via a protocol and receive a tradable token representing your stake, gaining flexibility but adding smart contract and protocol governance risk.
- Joining managed staking services: Professional operators run validators for you under non-custodial or semi-custodial models, often charging a fee for reduced operational hassle.

Pro Tip:Before you start staking, check how your local laws treat staking rewards and whether any reporting is required. Tax and regulatory treatment can vary widely by country and may affect which method makes sense for you.
Future of Proof of Stake and Evolving Designs
- Long-term security budgets: How PoS chains will maintain strong incentives for validators as inflation drops and fee markets evolve.
- Liquid staking centralization: Whether popular liquid staking tokens could concentrate voting power and create new systemic risks.
- Regulatory attention: How policymakers will treat staking rewards, validator responsibilities, and large staking providers in different jurisdictions.
- Interoperability and shared security: Ways PoS chains can share validator sets or stake to secure multiple networks and enable safer cross-chain activity.
- Home staking and inclusivity: Efforts to keep validator requirements low enough that individuals can still participate directly from consumer hardware.
Proof of Stake FAQ
Bringing It All Together
May Be Suitable For
- Long-term holders willing to lock or delegate some tokens for network security and rewards
- Users comfortable learning basic staking mechanics and validator selection
- People who value lower energy use and want to support PoS-based ecosystems
- Developers and power users building on PoS smart contract platforms
May Not Be Suitable For
- Traders who need full liquidity at all times and cannot tolerate lock-up periods
- Users unwilling to research validators, providers, or protocol rules before staking
- People with very low risk tolerance who cannot accept potential slashing or smart contract risk
- Anyone in a jurisdiction where staking may face unclear or restrictive regulation
Proof of Stake is a major step in the evolution of blockchain consensus. By replacing energy-intensive mining with capital at risk, it opens network security to a wider range of participants while dramatically reducing environmental impact. At the same time, PoS introduces new complexities around economics, governance, and operational risk. Slashing, lock-ups, and stake centralization are real issues that deserve careful attention. If you treat staking as a security role rather than just yield farming, you can choose methods and risk levels that match your skills and time horizon. Start small, learn the specific rules of each network, and scale up only when you are confident in both the technology and your own understanding.