Proof of Work (PoW) is a way for a decentralized network to agree on which transactions are valid without a central authority. In systems like Bitcoin, miners compete to solve a hard mathematical puzzle, and the first one to solve it earns the right to add a new block of transactions to the blockchain. This puzzle-solving race is what people usually call Bitcoin mining. It uses electricity and specialized hardware, but in return it makes it extremely expensive for anyone to rewrite history or fake transactions, because they would need to redo huge amounts of work. In this guide, you will see how PoW works step by step, why it is considered secure, and where its real weaknesses lie. You will also compare it with alternatives like Proof of Stake, so you can judge for yourself whether PoW-based coins fit your risk, values, and time horizon.
Proof of Work in a Nutshell
Summary
- PoW makes miners compete to find a valid hash for a block, and the winner adds transactions and earns newly issued coins plus fees.
- Security comes from the fact that rewriting history would require redoing as much or more work than the honest majority already performed.
- The system intentionally ties security to energy cost, which deters attackers but also creates environmental and political debates.
- Bitcoin has run on PoW since 2009, giving it one of the longest and most battle-tested security records in crypto.
- Many early altcoins like Litecoin and Monero also use PoW, while newer smart contract platforms often choose Proof of Stake instead.
- PoW networks are most robust when they have high total hashpower and a diverse set of independent miners or mining pools.
Grasping Proof of Work Through Analogies

Pro Tip:Analogies like lotteries or puzzle races simplify how Proof of Work feels, but they hide many details. Use them as mental anchors, not as exact descriptions. In the next section you will walk through the real steps a PoW blockchain follows, so you can connect the story in your head with the actual data structures, hashes, and incentives on the network.
How Proof of Work Actually Works (Step by Step)
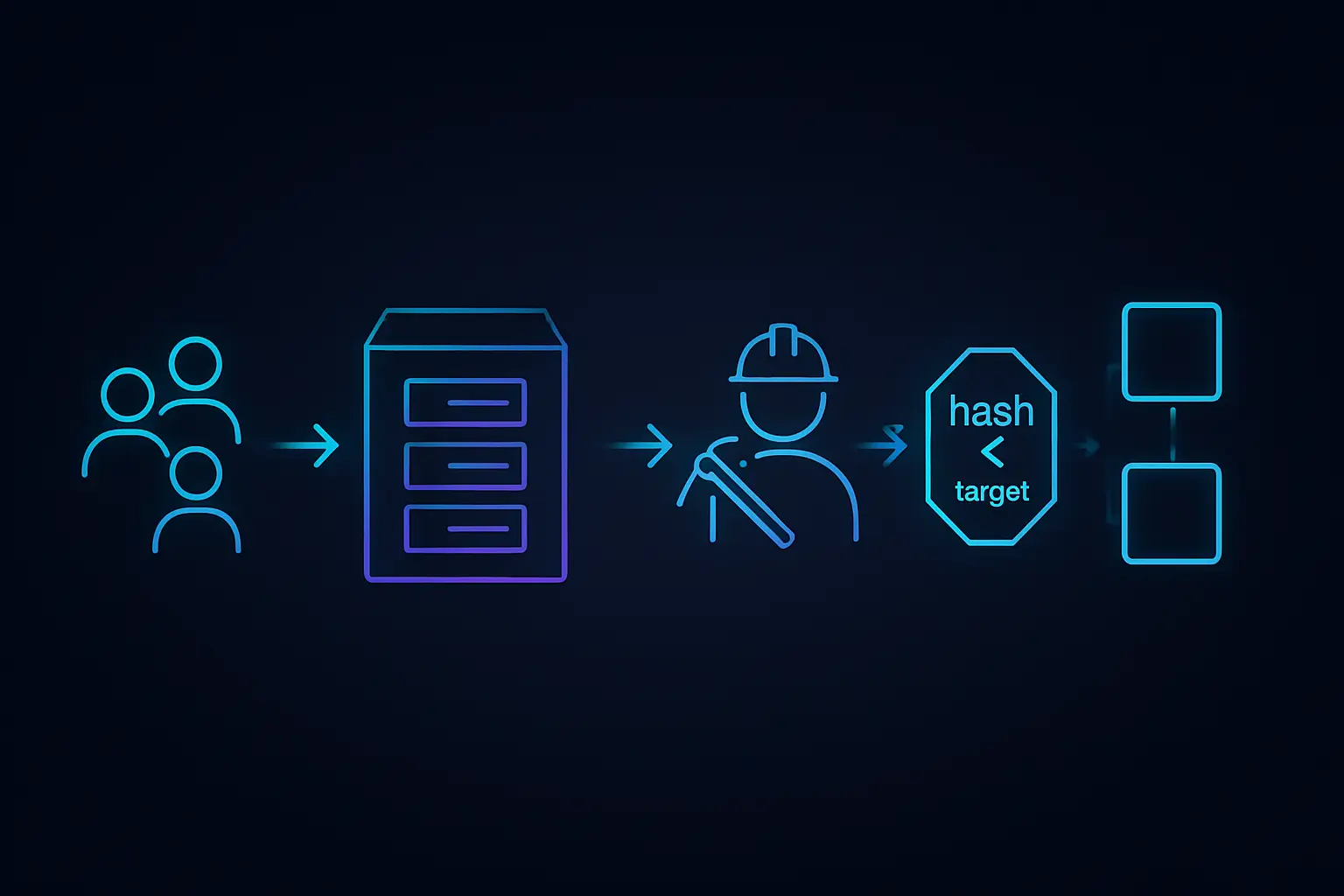
- Users broadcast transactions to the network, and nodes collect them into a waiting area often called the mempool.
- A miner selects a set of valid transactions from the mempool, adds a special coinbase transaction paying themselves the reward, and constructs a candidate block.
- The miner builds a block header containing, among other fields, a reference to the previous block, a Merkle root of all transactions, a timestamp, and a nonce value.
- The miner repeatedly hashes the block header, changing the nonce (and sometimes other small fields) to search for a hash that is below the current difficulty target.
- If the miner finds a valid hash that meets the difficulty target, they broadcast their new block and its proof of work to the network.
- Other nodes independently verify the block: they recheck all transactions, recompute the hash, and confirm it meets the difficulty target.
- If the block is valid, nodes add it to their local copy of the chain and treat its transactions as confirmed, usually after several more blocks are built on top.
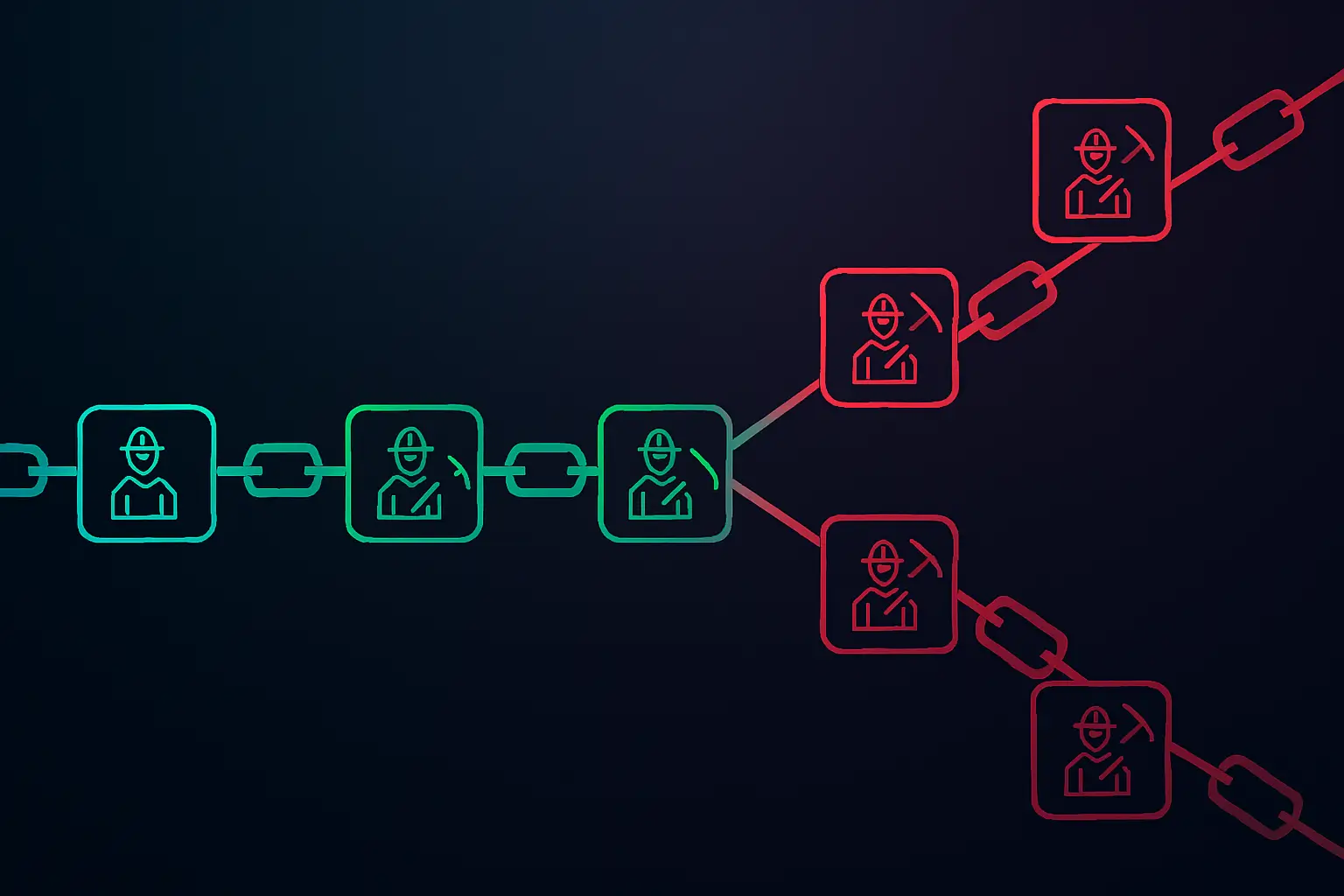
- When there are competing chains, nodes follow the chain with the most accumulated work (often the longest), which aligns everyone on a single history over time.
Under the Hood: Hashes, Difficulty, and Incentives
- Cryptographic hash functions like SHA-256 map any input to a fixed-size output that looks random, and are designed to be one-way and collision-resistant.
- Because hashes are unpredictable, the only way to find a hash below the difficulty target is brute-force trial and error, which is what miners perform with their hardware.
- The network periodically adjusts the difficulty target so that, on average, blocks arrive at a fixed rate (for Bitcoin, about every 10 minutes) regardless of how much hashpower is online.
- Miners are paid with a block reward (newly created coins) plus transaction fees, which must at least cover their electricity and hardware costs over time.
- Since honest mining earns predictable rewards while attacks risk huge costs and uncertain gains, rational miners are usually better off following the rules.
- If rewards fall too low or difficulty rules change abruptly, miners may switch off or move to other coins, which can weaken security and make attacks cheaper.
Pro Tip:PoW security is not just about math; it is about incentives. When a network changes block rewards, halving schedules, or difficulty rules, it is also changing miners’ profit calculations. If mining becomes unprofitable or too unpredictable, hashpower can leave, making attacks cheaper and centralization more likely. Always pay attention to a coin’s monetary and difficulty policy, not just its headline hash algorithm.
From Anti-Spam Idea to Bitcoin’s Security Backbone
The idea behind Proof of Work existed before Bitcoin and was originally proposed as a way to fight email spam. Systems like Hashcash asked senders to perform a small amount of computation per email, making mass spamming costly while keeping normal use affordable. Satoshi Nakamoto’s breakthrough was to reuse this concept not for email, but to secure a decentralized money system. By tying block creation to PoW, Bitcoin turned electricity and computation into a shield against double-spending and censorship.
Key Points
- 1990s–2000s: Researchers propose Proof of Work schemes like Hashcash to make sending spam or launching denial-of-service attacks more expensive.
- 2008: The Bitcoin whitepaper describes a peer-to-peer electronic cash system that uses PoW to reach consensus on transaction history without a central server.
- 2009: The Bitcoin genesis block is mined on CPUs, and early users mine casually on home computers to secure the network and earn coins.
- 2010s: Mining becomes industrial, moving from CPUs to GPUs to specialized ASICs, with large mining farms forming in regions with cheap electricity.
- Other cryptocurrencies such as Litecoin and Monero adopt PoW with different hash functions or goals, like faster blocks or stronger privacy.
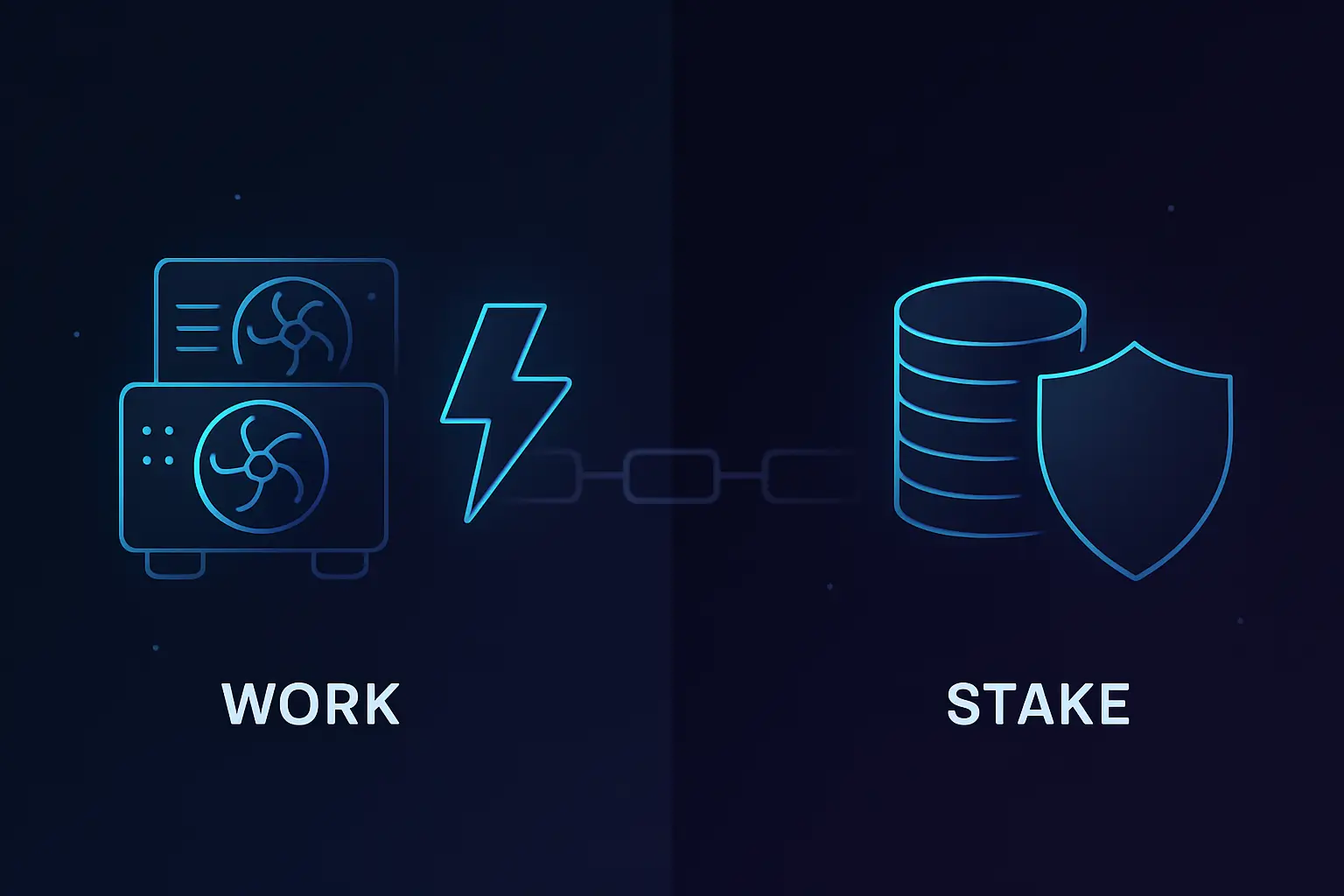
- 2022: Ethereum completes its transition from PoW to Proof of Stake, showing that large networks can change consensus mechanisms, but with major trade-offs and complexity.
Where Proof of Work Is Used Today
Today, Proof of Work is best known as the engine behind Bitcoin, which uses it to secure a global, permissionless monetary network. Several other major coins also rely on PoW, often with different design goals such as faster payments or stronger privacy. Beyond large caps, many smaller altcoins experiment with alternative PoW algorithms or hybrid designs. There are also non-monetary uses, where PoW helps create tamper-evident timestamps or protects public data from cheap spam and abuse.
Use Cases
- Bitcoin uses PoW to secure its monetary ledger, resisting censorship and double-spends across thousands of nodes worldwide.
- Litecoin and similar coins use PoW with different parameters (like faster block times) to target cheaper, quicker everyday payments.
- Monero relies on PoW within a privacy-focused design, aiming to keep mining more accessible to regular hardware and to hide transaction details.
- Smaller PoW coins experiment with novel hash algorithms or hybrid models, though their lower hashpower can make them more vulnerable to attacks.
- Timestamping and data anchoring services embed document hashes into PoW blockchains to prove that certain data existed at a specific time.
- Academic and hobbyist projects use PoW to study game theory, security assumptions, and the environmental impacts of different consensus designs.
- Hashpower marketplaces let people rent mining power temporarily, which can be used for legitimate mining or, in some cases, to attack weaker PoW chains.
Case Study / Story

Security Guarantees and Risks of Proof of Work
Primary Risk Factors
Proof of Work aims to make cheating more expensive than playing by the rules. To rewrite confirmed transactions, an attacker must control huge amounts of hashpower and pay for the electricity and hardware to outpace the honest majority. In practice, this model has worked well for large networks like Bitcoin, but it has limits. Smaller PoW coins with low total hashpower have suffered 51% attacks, and even big networks face concerns about mining pool concentration, energy footprint, and changing regulatory attitudes.
Primary Risk Factors
Security Best Practices
- PoW is only as strong as the hashpower, miner distribution, and incentives behind it. A famous brand or algorithm name does not guarantee safety. Before trusting a PoW coin, look at its total hashpower, how concentrated its mining is, and whether its economic design gives miners a reason to defend the network long term.
Pros and Cons of Proof of Work
Pros
Cons
Proof of Work vs. Other Consensus Mechanisms
How to Interact Safely with PoW Networks
- Start with well-established PoW coins that have high hashpower and good documentation, rather than obscure small-cap projects.
- Use reputable wallets that let you control your own keys, and learn basic security practices like backups and hardware wallets.
- Understand typical fee levels and confirmation times so you are not surprised by delays or overpaying during busy periods.
- If you try hobby mining, begin with educational goals and small budgets, and be skeptical of cloud-mining contracts that promise guaranteed returns.
- Check basic network health indicators such as total hash rate, mining pool distribution, and recent difficulty changes before making large transfers.
Proof of Work FAQ
Wrapping Up: When Does Proof of Work Make Sense?
May Be Suitable For
- Investors who prioritize censorship-resistant, long-term settlement over speed and features
- Users who value transparent, battle-tested security models like Bitcoin’s
- Technically curious people willing to learn how consensus and incentives work
Proof of Work turns electricity and computation into a public shield for digital value. By making it costly to rewrite history, it allows open networks like Bitcoin to function without banks or central operators, relying instead on transparent rules and incentives. This security comes with trade-offs: significant energy use, hardware concentration risks, and slower throughput than some newer designs. Large PoW networks have a strong track record, while smaller ones can be fragile if hashpower is low or easily rented. When you evaluate any crypto project, treat its consensus mechanism as a core part of its identity, not a technical footnote. Understanding how PoW works helps you decide when its guarantees are worth the costs for your own savings, values, and time horizon.